The only platform that guarantees sensitive data protection for critical infrastructure organisations
Ensure the protection of your business continuity and supply chains. Securely share customer data, system designs, IP and other confidential information internally and externally with zero risk of unauthorised access
Military-grade security with end-to-end encryption
Purpose-built for critical infrastructure organisations
IRAP assessed and independently audited
Are your file-sharing behaviours putting you at risk of operational disruption?
Storing and sharing data externally with suppliers, vendors, or third parties is vital for operations, but it is also one of the highest-risk activities for critical infrastructure organisations.
When critical infrastructure organisations experience data breaches or unauthorised access to confidential information, it can severely impact continuity of service, put customers at risk, and even become an issue of national security.
The Security Legislation Amendment (Critical Infrastructure) Bill 2020 states that all Australian critical infrastructure entities are required to identify, minimise and mitigate potential hazards to security.
3 red flags that put you at risk
![]()
You are still using email, internal portals or legacy transfer systems to transfer sensitive information between stakeholders.
![]()
You use encrypted tools, but they're not end-to-end encrypted, or your key management is complex and error-prone.
![]()
You use file sharing technology that is not compliant and doesn't have fail-safe auditability and chain of custody.
Ensure business continuity with guaranteed sensitive data protection
-
Communications
-
Utilities
-
Transport
-
Education & Research
-
Financial Services
Communications organisations (including Telcos) are required to store and share confidential information such as customer data, intellectual property (IP), and contracts. Breaches of this sensitive data can quickly lead to identity theft, financial fraud, and operational disruption that can shut down critical services.
Utilities organisations are constantly sharing sensitive information with suppliers and vendors to enable service delivery. To ensure supply chain security and business operations, they must manage cybersecurity risks associated with suppliers and third-party vendors (potential weak links) and secure their data and documentation from falling into the wrong hands.
Unauthorised access to transport organisations' operational data (including routes, schedules, timetables, and more) can present severe security risks and lead to operational shutdowns that impact the movements of millions of people.
Education and research establishments hold private and personal data of students and staff, as well as confidential information like patents, IP and system designs, making intellectual property protection vitally important.
Banks face existential threats, including unauthorised access to accounts, personal data breaches, and restrictions on large file transfers, which can all lead to catastrophic financial fraud and reputational risk.
A single, secure-by-design platform for critical infrastructure organisations
DekkoSecure provides granular access control and identity management, ensuring that only authorised individuals have access to critical systems and data through access controls, authentication methods, and identity management practices
End-to-end encryption
The DekkoSecure platform uses end-to-end military grade encryption (E2EE). All content is encrypted on the sender's device and decrypted on the recipient’s device. Content is never accessible to an unauthorised third party
Zero Knowledge
Zero Knowledge protocols are built into DekkoSecure’s collaboration features. Files are owned by the user and only they can choose who to share it with. Not even we can see shared or stored data, delivering true data ownership.
Key management
Users’ private keys are protected and kept confidential by their password, so users can be confident that their information is protected from unauthorised access.
Secure & compliant
DekkoSecure is hosted on Microsoft Azure triple-redundant cloud in Australia, which carries numerous compliance certifications such ISO, CSA, SOC and IRAP PROTECTED.
No file transfer limits
DekkoSecure is the only application to enable secure large file transfer of any size or type with no limits.
DekkoSecure helps organisations adopt the CIA triad
best-practice principles
The USA's National Institute of Standards and Technology has established best practices for data integrity, protecting assets against ransomware and other destructive events.
Those globally recognised best practices include adopting solutions that consider the CIA triad representing the three pillars of information security: confidentiality, integrity, and availability.
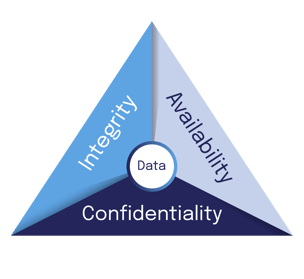
- Confidentiality - Preserving authorised restrictions on information access and disclosure, including means for protecting personal privacy and proprietary information.
- Integrity - Guarding against improper information modification or destruction and ensuring information non-repudiation and authenticity.
- Availability - Ensuring timely and reliable access to and use of information.
Five powerful tools on one secure platform
Protect your entire collaboration workflow with a single-minded approach to security.
Trusted by the most security-conscious organisations globally

